Governance
Governance is designed for credibility from day one: 2/3 multisig and a 48–72h timelock for critical changes. We publish addresses and logs, and expand participation as the network matures.
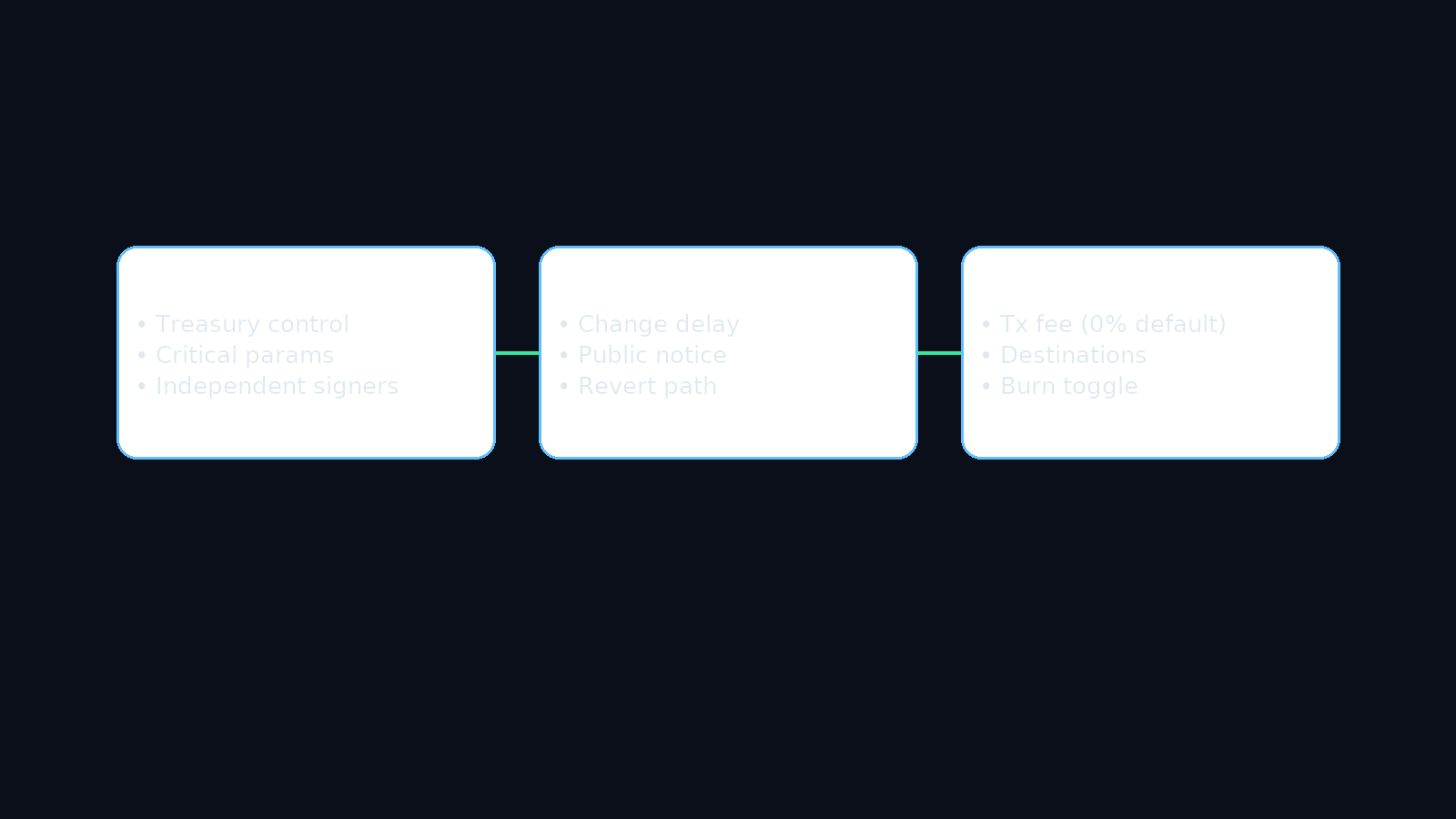
Multisig (2/3)
Independent signers. Controls treasury and sensitive parameters.
Timelock (48–72h)
Enforced delay for changes with public visibility before execution.
Scope
Transaction fee %, fee destinations, burn toggle. Token is non-upgradeable.
Principles
- Security first: Separation of duties, least privilege, defense in depth.
- Predictability: Changes require a delay window with public notice.
- Transparency: Publish addresses, logs, and monthly reports.
- Progressive decentralization: Expand participation as usage grows.
Roles & Responsibilities
- Signers (2/3): Execute approved changes; maintain key hygiene.
- Proposers: Draft change proposals, impact analysis, and notices.
- Auditors / Reviewers: Verify scope, simulate effects, and check logs.
- Community: Provide feedback; participate in off-chain signaling.
| Decision | Default | Who Approves | Controls |
|---|---|---|---|
| Transaction Fee % | 0% at launch | 2/3 multisig | 48–72h timelock, public notice |
| Fee Destinations | None at launch | 2/3 multisig | 48–72h timelock, public notice |
| Burn Toggle | Disabled | 2/3 multisig + policy approval | Timelock; scope-limited execution |
| Treasury Transfers | As budgeted | 2/3 multisig | Allowlist, limits per signer, logs |
Change Process
- Proposal: Write-up with rationale, scope, and risk analysis.
- Notice: Publicly announce intent; start 48–72h timelock.
- Review: Validate addresses, simulate impact, schedule execution.
- Execution: Multisig signs after the delay window; tx hash published.
- Post-change report: Summarize results and update documentation.
Transparency & Reporting
- Published addresses for token, multisig, vesting, and treasury.
- Monthly on-chain dashboards and written reports.
- Change logs: proposals, notices, execution tx hashes.
- Unlock schedule CSV/Excel available in the Data Room.
Emergency Controls
- Pausable emergency switch for modules outside the token when applicable.
- Runbooks for key revocation, module pause, and rollback.
- Responsible disclosure mailbox; bug bounty scope published.
Path to Broader Participation
As usage grows, we expand the circle of decision-makers. Off-chain signaling (e.g., Snapshot) can guide multisig decisions before they execute on-chain parameters.